sweat pores and ridge contours.

International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 289
ISSN 2229-5518
Key words: - Minutiae points, Ridges, Furrows, Bifurcation, Termination, Orientation detection, Region of interest (ROI).
1. INTRODUCTION: - Biometric based recognition is the science of identifying or verifying the identity of a person based on physiological and or behavioral characteristics. Physiological traits are related to the physiology of the body and mainly include Fingerprint, face, DNA, ear, iris, ret ina, hand and palm geometry. Behavioral traits are related to behavior of a person and examples include signature,
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 290
ISSN 2229-5518
typing rhythm, gait, voice etc. Biometric recognition offers many advantages over traditional PIN number or password and token-based (e.g., ID cards) approaches. A biometric trait cannot be easily transferred, forgotten or lost, the rightful owner of the biometric template can be easily identified, and it is difficult to duplicate a biometric trait.
There are a number of desirable properties for any chosen biometric characteristic. These include:
1. Universality: Every person should have the characteristic.
2. Uniqueness: No two persons should be the same in terms of the biometric characteristic.
3. Permanence: The biometric characteristics should not change, or change minimally, over time.
4. Collectability: The biometric characteristic should be measurable with some (practical) sensing device.
5. Acceptability: The user population and the public in general should have no (Strong) objection to the measuring/collection of the biometric trait.
A biometric system is essentially a pattern recognition system that operates by Acquiring biometric data from an individual, extracting a feature set from the acquired Data and comparing this feature set against the template set in the database. Depending on the application context, a biometric system may operate either in Verification mode or identification mode.
The effectiveness of a biometric system can be judged by following characteristics: Performance, Scalability.
A fingerprint is an impression of the friction ridges, from the surface of anger-tip. Fingerprints have been used for personal identification for many decades, more recently becoming automated due to advancements in computing capabilities. Fingerprint recognition is nowadays one of the most important and popular biometric technologies mainly because of the inherent ease in acquisition, the numerous sources (ten fingers) available for collection, and the established use and collections by law enforcement agencies. Automatic fingerprint identification is one of the most reliable biometric technologies. This is
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 291
ISSN 2229-5518
because of the well known fingerprint distinctiveness, persistence, ease of acquisition and high matching accuracy rates. Fingerprints are unique to each individual and they do not change over time. Even identical twins (who share their DNA) do not carry identical fingerprints. The uniqueness can be attributed to the fact that the ridge patterns and the details in small areas of friction ridges are never repeated.
The types of information that can be collected from a fingerprint's friction ridge impression can be categorized as Level 1, Level 2, or Level 3 features.
Level 1 feature comprises these global patterns and morphological information. They alone do not contain sufficient information to uniquely identify fingerprints but are used for broad classification.
Level 2 features or minutiae refer to the various ways that the ridges can be discontinuous. These are essentially Galton characteristics, namely ridge endings and ridge bifurcations. A ridge ending is defined as the ridge point where a ridge ends abruptly. A bifurcation is defined as the ridge point where a ridge
bifurcates into twoIridgesJ.
SER
Level 3 features are the extremely fine intra ridge details present in fingerprints. These are essentially the
sweat pores and ridge contours.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 292
ISSN 2229-5518
A fingerprint consists of two basic types of minutiae, ridge endings and bifurcations. The minutiae and their relative positions to each other are then used for comparisons. It is therefore evident that the more accurate the process of extraction of minutiae, the more accurate and reliable the entire automated fingerprint recognition system becomes.
Here we introduce various fingerprint representations and provide a general review of image enhancement, feature extraction, and matching techniques that are used in Minutiae-based fingerprint recognition systems.
This representation relies on the ridge structure, global landmarks and ridge pattern characteristics, Such as the singular points, ridge orientation map, and the ridge frequency map.
This is the most widely used and studied fingerprint representation. Local ridge details are the
discontinuities of local ridge structure referred to as minutiae. Among minutiae types, “ridge ending” and “ridge bifurcation” are the most used, since all other types of minutiae can be seen as the combinations of “ridge endings” And “ridge bifurcations”.
On every ridge of the finger epidermis, there are many tiny sweat pores. Pores are considered to be highly distinctive in terms of their number, positions, and shapes. However, extracting pores is feasible only in high-resolution fingerprint images (for example 1000 DPI) and with good image quality. Therefore, this
kind of representation is not practical for most applications.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 293
ISSN 2229-5518
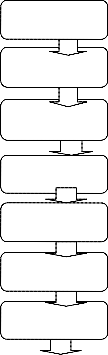
Load image
Enhancement
Binarize
Remarks
Process1
Process2
Termination
Orientation
Bifurcation
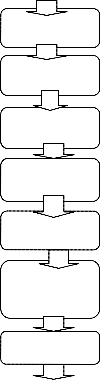
Orientation
Thinning
Minutiae
Termination
Process3
ROI Suppress
minutiae
Validation
Save
Minutiae match
Bifurcation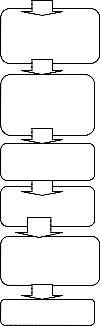
IJSEGUI R
Orientation
We have proposed some algorithms to find out the minutiae points. With the help of the algorithms, we have found the ROI (Region of interest).in the above DFD we have discussed all the stages of load image, enhancement, binarize, thinning, minutiae points etc. here we have proposed the algo. to find out termination and bifurcation points.
1: Break the image pixel in 3X3 window. matlab code fun=@minutiae; L = nlfilter(K, [3 3], fun);
2: while all 3X3 windows are not computed repeat steps 3 and 4
3: check if central pixel has only one neighbor
4: Mark it as red circle in image and store its location attributes.
5: end
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 294
ISSN 2229-5518
1: Break the image pixel in 3X3 window. matlab code fun=@minutiae; L = nlfilter (K, [3 3], fun);
2: while all 3X3 windows are not computed repeat steps 3 and 4
3: check if central pixel has three neighbor pixels
4: Mark it as green circle in image and store its location attributes.
5: end.

IJSER
Figure 2(a) & 3(b) Here with the help of bifurcation and termination algorithm the termination and bifurcation points are found (Red circles are the termination points and green circle are the bifurcation points).
We have a lot of spurious minutiae. We are going to process them. Process 1: if the distance between a termination and a bifurcation is smaller than D, we remove this minutiae process 2: if the distance between two bifurcations is smaller than D, we remove this minutia process 3: if the distance between two
terminations is smaller than D, we remove this minutiae.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 295
ISSN 2229-5518
If the distance between a termination and a bifurcation is smaller than D find minutiae and remove them for Bifurcation and termination.
If the distance between two bifurcations is smaller than D find minutiae and remove them from
Bifurcation and termination.
If the distance between two terminations is smaller than D find minutiae and remove them from
Bifurcation and termination.
IJSER
Figure 3 Remark for Process 1,2 & 3.
We have to determine a ROI. For that, we consider the binary image, and we apply a closing on this image and erosion. With the GUI, we allow the use of ROI tools of MATLAB, to define manually the ROI.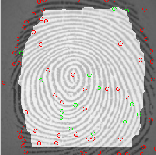

IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 296
ISSN 2229-5518
Figure 4 :ROI(Region of interest)
Once we defined the ROI, we can suppress minutiae external to this ROI.
Figure 5: Special minutiae points in ROI
Once we determined the different minutiae, we have to find the orientation of each one.
We have to find the orientation of the termination. For finding that, we analyze the position of the pixel
on the boundary of a 5 x 5 bounding box of the termination. We compare this position to the Table variable. The Table variable gives the angle in radian. & the table will be maintained in MATLAB.
Figure 6: Termination orientation
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 297
ISSN 2229-5518
For each bifurcation, we have three lines. So we operate the same process than in termination case three times.
Figure 7: Bifurcation orientation
IJSER
In this step, we validate the minutiae (GUI)
In this step, we are going to save the minutiae in a file
Given two set of minutia of two fingerprint images, the minutia match algorithm determines whether the two minutiae sets are from the same finger or not.
Two steps: 1. Alignment stage 2. Match stage
1. Ridge bifurcation and endings
2. False minutiae rejection based on distance from ridges.
3. Orientation field of minutiae terms based on a) Termination
b) Bifurcation
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 298
ISSN 2229-5518
4. ROI(Region of interest)
5. Suppress minutiae points
Among all these things, Region of Interest of the image is carried out in an autonomous way, which makes the work fitted to reconstruction and recognition phases.
Here we have proposed the fingerprint minutiae extraction idea with ROI concept which is based on Minutiae extraction and orientation detection .Actual phases in the proposed work consist of binarization and thinning to extract the image constituents from the image details. After those minutiae terms are determined on the basis of bifurcation and termination which occurs at the ridges in the fingerprint. False minutia terms are rejected by again comparing that with ROI and user selectivity has been introduced in case user wants to select its own ROI. The experimental results show that the fingerprint is very consistent with the original fingerprint and that there is a high chance of deceiving a state of the art commercial fingerprint recognition system. The fingerprints still contain a few spurious Minutiae, especially in the high-curvature regions. To overcome this problem, a better model for the continuous phase of fingerprints of any pattern type should be developed. To obtain reconstructed fingerprint that are even more consistent with the original fingerprints, ridge frequency and minutiae type should be utilized. To make the reconstructed fingerprints appear visually more realistic, brightness, ridge thickness, pores, and noise should be modeled. The accept rate of the reconstructed fingerprints can be further improved by reducing the image quality around the spurious minutiae .In this paper the image extraction and enhancement is further more adopted to make the competitive edge on the fingerprint market. Experiments demonstrate the details of orientation and minutiae terms of a particular fingerprint image in a detailed text file which furthermore can be used for database of the persons and recognition. Results are matched with consistency and lacks in image enhancement images used are of good resolution and hence must be revised on this case for future. All these have become motivation for the development of further improved forensic techniques.
[1] Fourth International Fingerprint Verification Competition. http://bias.csr. Unibo.it/fvc2006. [2] The History of Fingerprints. http://www.onin.com/fp/fphistory.html.
[3] Neurotechnology Sample Database. http:// www.Neurotechnology.Com/ download.html.
[4] Ridges and Furrows - history and science of fingerprint identification, technology and legal issues. http://ridgesandfurrows.homestead.com/ fingerprint html.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 1, January-2014 299
ISSN 2229-5518
[5] FVC2004 - Third International Fingerprint Verification Competition. http://
bias.csr.unibo.it/fvc2004, 2004.
[6] CDEFFS: The ANSI/NIST Committee to Define an Extended Fingerprint Feature Set. http : //
fingerprint.gov/ standard/ cdeffs/ index. html, October 2006.
[7] The Thin Blue Line. http://www.policensw.com/info/fingerprints/finger 06.html, October 2006.
[8] E. M. Arvacheh and H. R. Tizhoosh. Pattern Analysis using Zernike Moments. In Instrumentation and Measurement Technology Conference, pages 1574{1578, May 2005}
[9] D.R. Ashbaugh. Quantitative-Qualitative Friction Ridge Analysis: An Introduction to Basic and
Advanced Ridgeology. CRC Press, 1999.
[10] A.M. Bazen and S.H. Gerez. Segmentation of fingerprint images. In Pro RISC 2001 Workshop on
Circuits, Systems and Signal Processing, pages 276{280.Citeseer, 2001}
[11] Mayank Vatsa, Richa Singh, Afzel Noore, and Max M.Houck. Quality-augmented fusion of level-
2 and level-3 fingerprint information using DSm theory.Int. J. Approx. Reasoning, 50(1):51{61,
2009}
[12] P. Ying-Han, T.B.J. Andrew, N.C.L David, and F. S. Hiew. Palmprint Verification with Moments.
Journal of Computer Graphics, Visualization and Computer Vision (WSCG), 12(1-3):325{332, Febuary 2003}
[13] F. Zernike. Beugungstheorie des schneidenverfahrens und seiner verbesserten form, der phasenkontrastmethode, 1:689{704, 1934}
[14] Tsai-Yang Jea, Minutiae-Based Partial Fingerprint Recognition, Department of Computer
Science & Engineering, November 2005.
[15] IEEE Transaction on pattern analysis and machine intelligence, VOL.33, NO. 2, Fingerprint reconstruction: From Minutiae to phase, Jianjiang Feng, Member IEEE & Anil K Jain, IEEE Fellow.
[16] A HIERARCHICAL FINGERPRINT MATCHINE SYSTEM, By Abhishek Rawat, to the
Department of Computer Science and Engineering, Indian Institute of Technology, Kanpur July 2009.
IJSER © 2014 http://www.ijser.org