International Journal of Scientific & Engineering Research, Volume 5, Issue 6, June-2014 168
ISSN 2229-5518
Enhanced Geometric – Based Hand Recognition
Using Neural Network
Dr. Haithem A. Alani
University of Al-Nahrain College of Science
Computer Science Department
ABSTRACT -- Person identification and verification using biometric methods is getting more important in today’s information society; Hand geometry techniques are simple easy and inexpensive in image acquisition. In this work hand image are preprocessed so that a simple hand shape is produced to extract hand geometry features, the features were normalized to eliminate the image size effect on the features. The average value of each feature in the database was used to binaries the feature, a feedforword neural network was used for hand recognition, the results obtained showed that the features which were extracted is very discriminative and good training to the neural network results in high degree of accuracy in recognition.
Keywords: hand geometry, biometric, feature extraction, neural network, Identification.
1. INTRODUCTION
Because of the increased hygiene concern in biometric systems and the difficulty in recognizing fingerprints of manual laborers and elderly people, hand geometry has been currently employed in many systems for personal verification mostly as a complement to finger-print authentication.[1]
While finger printing and iris based systems work well for high security applications, they are not as suitable for medium and low security applications because of privacy concerns. Individual hand features are not descriptive enough for identification because hand geometry is not so distinctive, so it is good way to provide authentication rather than identification for someone [2]. Hand Geometry based verification systems find more acceptance because hand geometry is not considered distinctive enough to establish a positive identity.[3]
Combining hand geometry with fingerprints and palm prints in a multi modal system can prove very useful in high security applications. The advantage of combining these features lies in the fact that while taking the data for hand geometry, the data for fingerprints and palm prints can be collected simultaneously. There will be no extra inconvenience to the user while the accuracy of the system may be greatly increased due to the addition of several more features. [4]
Among all kinds of biometrics techniques, hand shape bio- metrics has drawn wide attention from researchers, and has been investigated for a long time [5]. As often noted in the literatures, hand shape biometrics is attractive due to its following advantages [5,6]:
(1) It is user-friendly since hand shape can be captured in a relatively convenient, non-intrusive manner by using inexpensive sensors.
(2) Other hand features such as palmprint, palm vein and knuckleprint can be easily integrated to an existing hand shape based biometric system to form a more robust multimodal biometrics system.
(3) It is more acceptable to the public mainly because it lacks
criminal connotation.
(4) It is less prone to disturbances and more robust to environmental conditions and to individual anomalies. [7]
In this work we proposed using hand geometry
In this research images from 'The Hong Kong Polytechnic University Contact-free 3D/2D Hand Images Database (Version1.0)' were used to build the database, three images of fifty persons were selected from the database.
2. RELATED WORK
Rong proposed a novel hand shaped recognition based two classical shape representations contexts and Inner distance they achieve high rate of identification, [7]
Bhuyan proposed a novel approach for hand pose recognition by using key geometrical features of hand they found that the proposed method is suitable for Human Computer Interactions. [8]
Oden proposed using implicit polynomials in object modeling and recognition for recognizing hand shape. And found it very successful. [9]
Erdem comparatively assessed two features, Hausdorff distance of the hand contours and independent component features of the hand silhouette images. Both the classification and the verification performances are found to be very satisfactory. [10]
Juan and others proposed the use of the morphological pattern spectrum or pecstrum, as the base of a biometric shape-based hand recognition system. The obtained results indicate that the pattern spectrum represents a good feature extraction alternative for low- and medium-level hand-shape-based biometric applications. [11]
3. DESCRIPTION OF HAND RECOGNITION SYSTEM
Since the matching is performed by using data of features
extracted from the hand images, many process are performed to make the features available, these process can be divided into the following three main steps:
1. Preprocessing stage in which all the required operations are implemented on the input image to make it ready to next step, that include transforming the image to gray, edge detection and thinning.
2. Feature extraction stage in which a trace to the hand
edge is performed to locate the fingers tip points, fingers base points and the start of hand points. Then the necessary arithmetic operations are done to locate the hand center and find the feature lines length.
3. Building the database stage in which all operations are done on features data to make it ready to be dealt with in database.
The above operations will be explained in the next sections.
3.1 Preprocessing
Many processes must be implemented on the hand image to make it ready for feature extraction these processes are:
• Convert the RGB values to grayscale values by forming a weighted sum of the R,G, and B components:
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 6, June-2014 169
ISSN 2229-5518
Igray = 0.2989 * R + 0.5870*G + 0.1140 * B [12]
• Edge detection: Canny’s edge detection algorithm is computationally more expensive compared to Sobel, Prewitt and Robert’s operator. However, the Canny’s edge detection algorithm performs better than all these operators under almost all scenarios.
The canny edge detector first smoothes the image to
eliminate and noise. It then finds the image gradient to highlight regions with high spatial derivatives. The algorithm then tracks along these regions and suppresses any pixel that is not at the maximum (nonmaximum suppression). The gradient array is now further reduced by hysteresis. Hysteresis is used to track along the remaining pixels that have not been suppressed. Hysteresis uses two thresholds and if the magnitude is below the first threshold, it is set to zero (made a nonedge). If the magnitude is above the high threshold, it is made an edge. And if the magnitude is between the 2 thresholds, then it is set to zero unless there is a path from this pixel to a pixel with a gradient above T2. [12]
• Edge thinning is a technique used to remove the unwanted spurious points on the edges in an image. Its advantage is to sharpen and thin edges which lead to greater efficiency in object recognition. It should be applied carefully such that removing the points will not cause to disconnect its neighbors in any way.
From the previous step we get a “segmented” image (an image with foreground pixels labeled 1 and background pixels labeled zero), trace boundary of the image by starting at a pixel (start pixel) and find the next pixel connected to the start pixel name the new pixel as start pixel repeat the process until no more start pixels are generated, the set of pixels found from the previous process is the boundary of the hand.
The boundary of the hand will be used in the next step of feature extraction.
3.2 Features Extraction
After obtaining the hand edge, the hand edge image will be
traced to find the locations of the fingers tip points, fingers
base points and start of palm points, figure (1) shows the hand edge image with the points:
1. The fingers tip: these are the location of top points of the five fingers denoted by points (A,B,C,D,E).
2. The fingers base points: the location of seven joint points of the hand denoted by points (F, G, H, I, J, K, L).
3. The start of palm points: the location of joint points
between the palm and the wrist denoted by points (M, N).
4. An additional point was calculated which represent the center of the circle that can be formed from the three points which are the base of between figure one and two, and two and three, and three and four denoted by points (I, J, K).
We call the center of this circle in this research the center of the hand.
The following distances were calculated from the locations of the above points:
1. Lines between the hand center and the fingers tips (five values).
2. Lines between hand center and fingers base points (five values after eliminating two values which were used for forming the circle.)
3. Lines between finger base points and fingertip (ten values).
4. Lines between hand center and palm start points. (Two values).
5. Lines between the finger base points (five values).
6. Lines parallel to base lines of the fingers passing through the mid-point of the line connecting the middle point of the base line and the head of the finger (five values) Examples of these lines are shown in the figure (1)
Z is the middle point of line IH
Line XY is parallel to line IH from the mid point of line
BZ
7. Three more lines lengths are found line IK, Line HL, and line FL
Which gives a total of thirty five lines which we assume to be the hand features. The features where first normalized by dividing them by the distance between the hand center and the third fingertip.
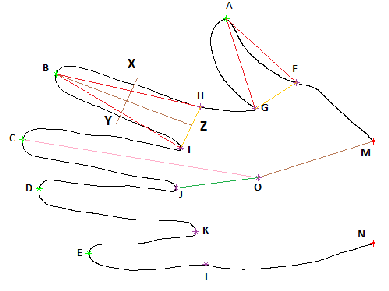
Figure (1) Hand Edge Shape
Points (A,B,C,D,E) fingers tips, Points (F,G,H,I,J,K,L) fingers base points, Points (M,N) start of palm points, Point O is the center of the circle formed from points (I,J,K)
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 6, June-2014 170
ISSN 2229-5518
4. HAND IMAGES DATABASE
In case of building the feature vectors database three different
images for the same hand were used from the input database as shown in figure (2). For each image:
• the hand edge is found, and the points explained in 3.2 are located
• the lines length explained in 3.2 are found, and normalized as explained.
the above lines length are found for each of the three images and the average value of the normalized length of each line in the three images is considered as a feature of the hand.



Figure (2) three different image of the same hand
A total of fifty different hand with three different images for each hand were used to build the database using images from the source [13].
The average value of each feature where calculated for all the hands images in the database.
𝑛
𝑎𝑣𝑒𝑟𝑓𝑒𝑎𝑡𝑢𝑟𝑒𝑖 = (�𝑗=1�𝑓𝑒𝑎𝑡𝑢𝑟𝑒𝑖𝑗 � )/n
The values where converted to binary value using the
following equation:
Valuei,j=1 if featurei,j > averfeaturei
Otherwise Valuei,j= 0.
where n is number of hands,Valuei,j the binary value of the feature j for the i,th hand in database, and featurei,j the normalized value of the feature j for the i,th hand in database and averfeaturei is the avarege value of the j,th feature of the hand.
5. RECOGNITION PHASE
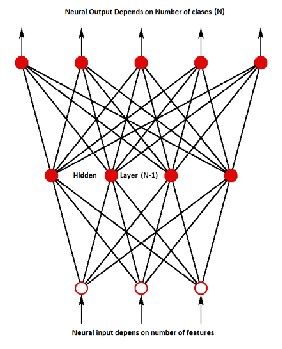
A feedforward neural network is a biologically inspired classification algorithm. It consist of a (possibly large) number of simple neuron-like processing units, organized in layers. Every unit in a layer is connected with all the units in the previous layer. These connections are not all equal, each connection may have a different strength or weight. The weights on these connections encode the knowledge of a network. Often the units in a neural network are also called nodes as shown in figure (3)
Data enters at the inputs and passes through the network, layer by layer, until it arrives at the outputs. During normal operation, that is when it acts as a classifier, there is no feedback between layers. This is why they are called feed forward neural networks. The FFNet uses a supervised learning algorithm: besides the input pattern, the neural net also needs to know to what category the pattern belongs.
Because real-life data many times contains noise as well as partly contradictory information these hopes can only be partly fulfilled.
A pattern, presented at the inputs, will be transformed from layer to layer until it reaches the output layer. Now
classification can occur by selecting the category associated with the output unit that has the largest output value.
The input data is divided into training, validation and test sets. The training set is used to update the network, the validation set is used to stop the
Figure (3) Feedforward Neural Network
network before it overfits the training data, thus preserving good generalization. The test set acts as a completely independent measure of how well the network can be expected to do on new samples.
Training stops when the network is no longer likely to improve on the training or validation sets.
Because we would like the network to not only recognize perfectly identical position of hand images. So we will try training a second network on noisy data as well as perfect data and compare its ability to generalize with the first network.
Network 1, trained without noise, has more errors due to noise than does Network 2, which was trained with noise.
IJSER © 2014 http://www.ijser.org
International Journal of Scientific & Engineering Research, Volume 5, Issue 6, June-2014 171
ISSN 2229-5518
it is noticed that when network was trained with noisy data it gives perfect results even when test data is at 0.2 of noise level and gives 95% correct results when noise level at 0.3. Figure (4) shows the neural network behavior with the noise level in input data.
6. CONCLUSION
Hand geometry techniques are simple easy and inexpensive
in image acquisition compared to fingerprint and iris image acquisition. Most sources described hand geometry as biometric that is user friendly but not accurate enough for high security applications, however in this research the data extracted from the hand images shows that hand geometry is a good and reliable biometric. The data extracted relies on how accurate the hand edge obtained from the hand image for that reason the preprocessing done on hand images had good effect on recognition accuracy, also the use of three images for each hand has reduce the effect of slight hand movements in the image capturing stage.
The use of the neural network trained on data exerted from the hand images with additional random noise added to the
data has a clear improvement on the discriminative accuracy of the network.
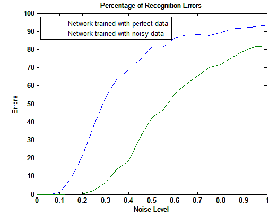
Figure (4)
Neural Network behavior with data
REFRENCES
[1] Xiaoqian Jiang ‘NEW DIRECTIONS IN CONTACT FREE HAND RECOGNITION’, IEEE
International Conference on Image Processing, 2007
[2] Amit Kumar Singh ‘Hand Geometry Verification System: A Review’ IEEE Ultra Modern Telecommunications and Workshops, 2009
[3] Yaroslav Bulatov ‘Hand recognition using geometric classifiers’ D.Zhang and A.K. Jain (Eds.) ICBA 2004, LNCS 3072, pp.753-959, 2004.
[4] Saraf Ashish ‘Design of a Hand Geometry Based Recognition System’ A Thesis to Department of Computer Science & Engineering, Indian Institute of Technology Kanpur,
Jan 2007
[5] N. Duta, ‘A survey of biometric technology based on hand shape’, Pattern Recognition 42 (11) (2009) 2797–
2806.
[6] E. Yoruk, H. Dutagaci, B. Sankur, Hand biometrics, Image and Vision Computing 24 (5) (2006)
[7] Rong-Xiang Hu ‘Hand shape recognition based on coherent distance shape contexts’ Pattern Recognition
45 (2012) 3348–3359
[8] M.K. Bhuyan ‘Hand Pose Recognition Using Geometric Features’ IEEE National Conference on Communications (NCC), 2011
[9] Cenker Öden ‘Hand Recognition Using Implicit Polynomials and Geometric Features’ Third International Conference, AVBPA Sweden, 2001
[10] Erdem Yörük ‘Shape-Based Hand Recognition’
IEEE TRANSACTIONS ON IMAGE PROCESSING, VOL. 15, NO. 7, JULY 2006
[11] Juan Manuel Ramirez-Cortes ‘Shape-based hand
recognition approach using the morphological pattern spectrum’ Journal of Electronic Imaging 18(1), 013012 (Jan–Mar 2009)
[12] R. C. Gonzalez ‘Digital Image Processing’ 3rd
Edition Prentice Hall (Augest 31,2007)
[13] Hong Kong University of Science and Technology
Hand Image Database AVBPA'2003)
IJSER © 2014 http://www.ijser.org





